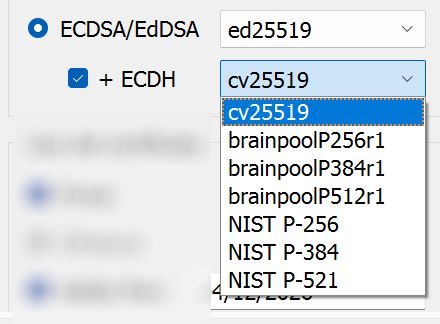
HI. When I create a new OpenPGP key pair (File->New Key Pair OpenPGP), in Advanced Settings I can choose ed25519/brainpool/NIST, but there is no ed/cv448 option. Why?
If I do it from the command line (C:\Program Files (x86)\GnuPG\bin\gpg --expert --full-gen-key) I can do it, choosing (9) ECC → (2) Curve 448.
I read all the Kleopatra doc, the GnuPG doc, I also downloaded the source code of both Kleopatra and GPG to try to understand, I explored the “default-new-key-algo” option (which I tried to set as “ed448/cert,sign+cv448/encr”, but without result) and read many forums on the internet, in short, hours of testing and research but I didn’t understand why it doesn’t show the ed448/cv448 option but only 25519.
Yet 448 it is an algorithm that has been supported for at least 2 years.
Where is the problem? how do I activate it on Kleopatra, without needing to use the command line?
Thank you